
Willard Jansen
Security Researcher & Penetration Tester

Security Researcher & Penetration Tester
Security researcher focused on finding and responsibly disclosing vulnerabilities in web applications and APIs. I combine manual testing with custom tooling to uncover issues that automated scanners miss — from authentication bypasses to business logic flaws.
Purpose-built tooling for the tests that matter
Most security testing relies heavily on automated scanners. I built Spectre — a proprietary, internal testing platform with dedicated labs and attack template libraries for complex, hard-to-test attack surfaces. Where scanners stop, manual testing with the right tooling takes over. Spectre is not publicly available.
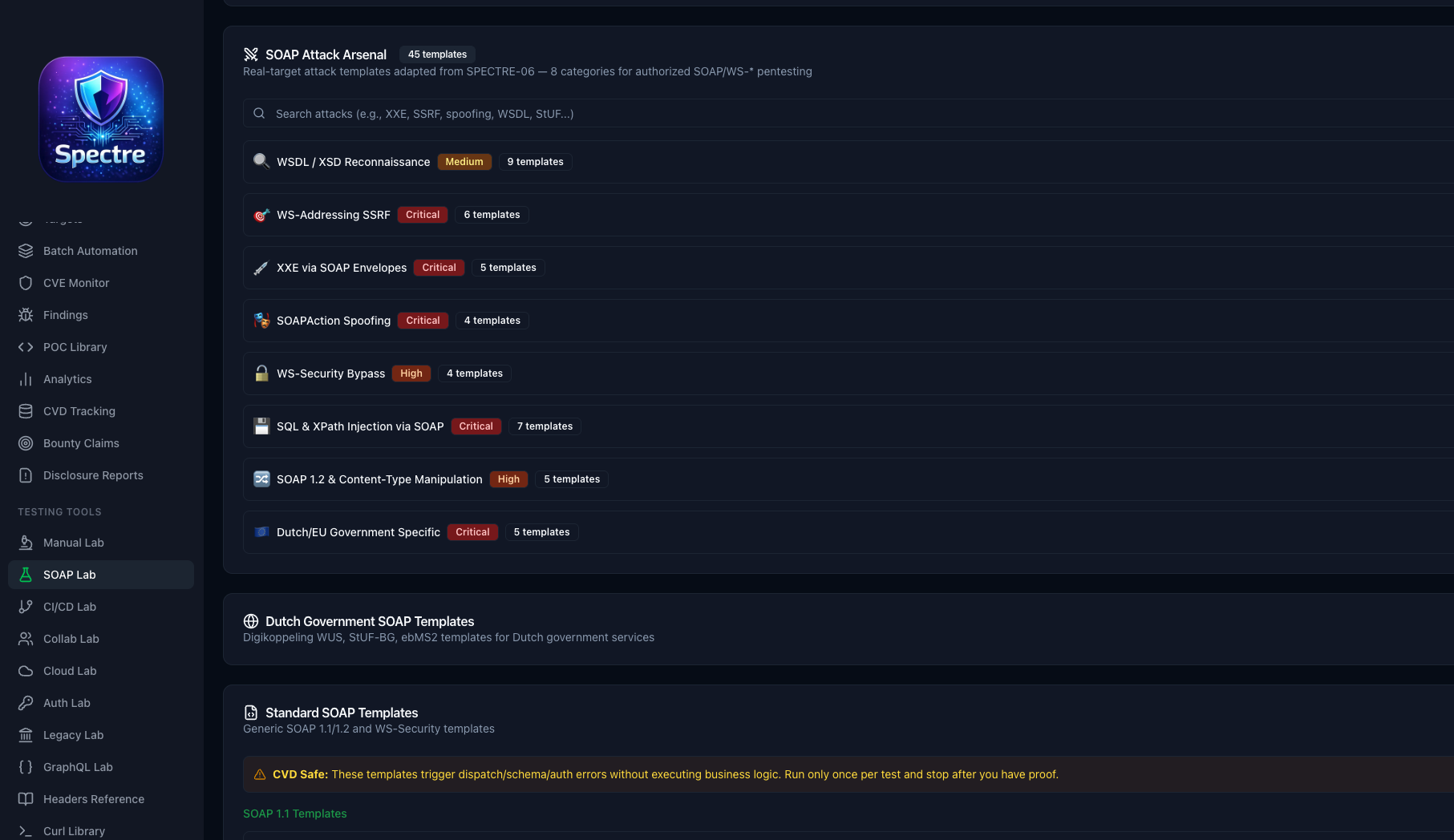
45+ attack templates for SOAP/WS-* services — XXE injection, WS-Addressing SSRF, SOAPAction spoofing, XPath injection, and Dutch government-specific protocols like StUF and ebMS2.
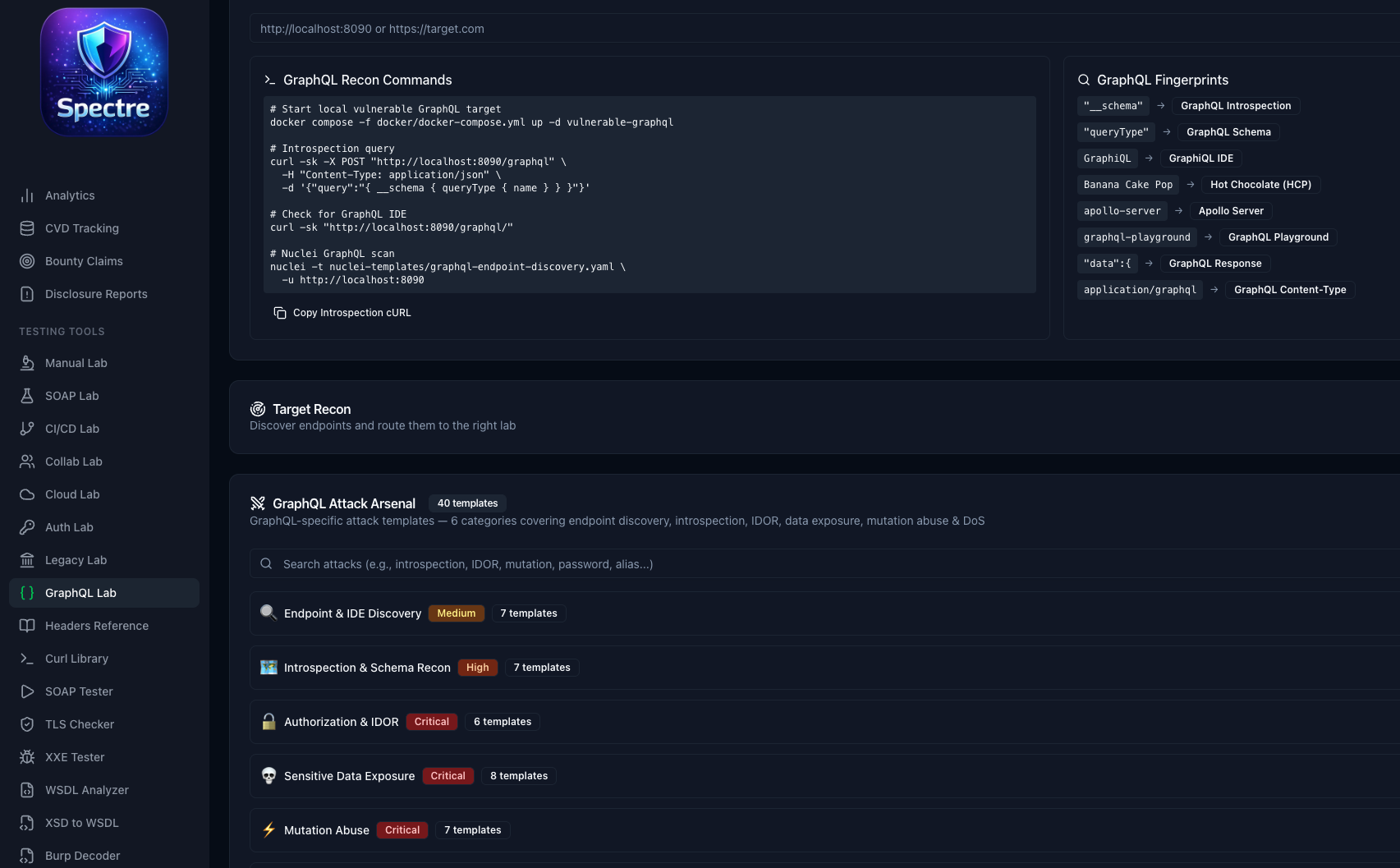
40+ attack templates for GraphQL APIs — introspection abuse, authorization & IDOR testing, sensitive data exposure, mutation abuse, and fingerprinting across Apollo, HCP, and other server implementations.
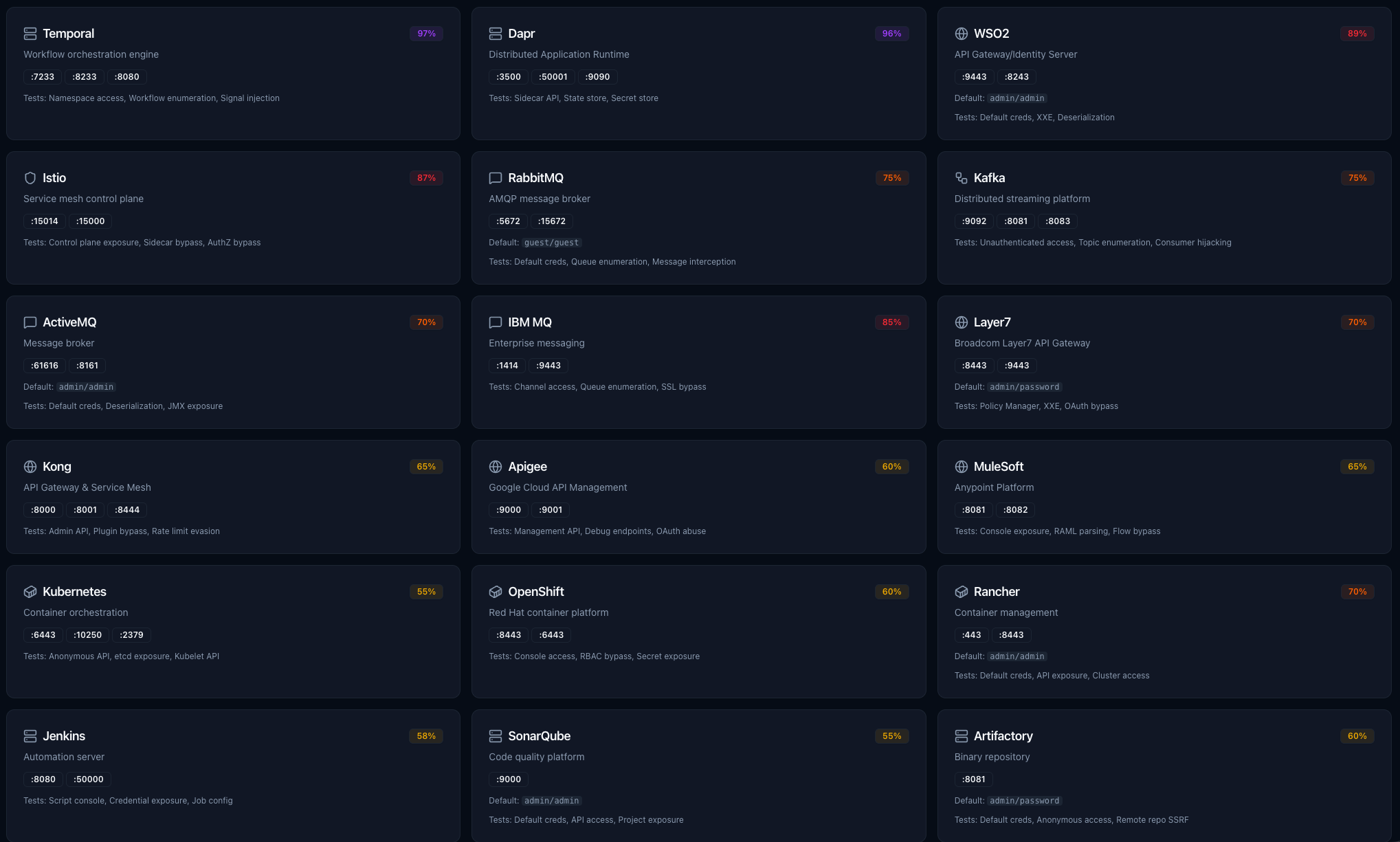
Preconfigured test environments for 21+ enterprise platforms — API gateways, message brokers, service meshes, container orchestration, and CI/CD infrastructure with ready-to-run test templates.
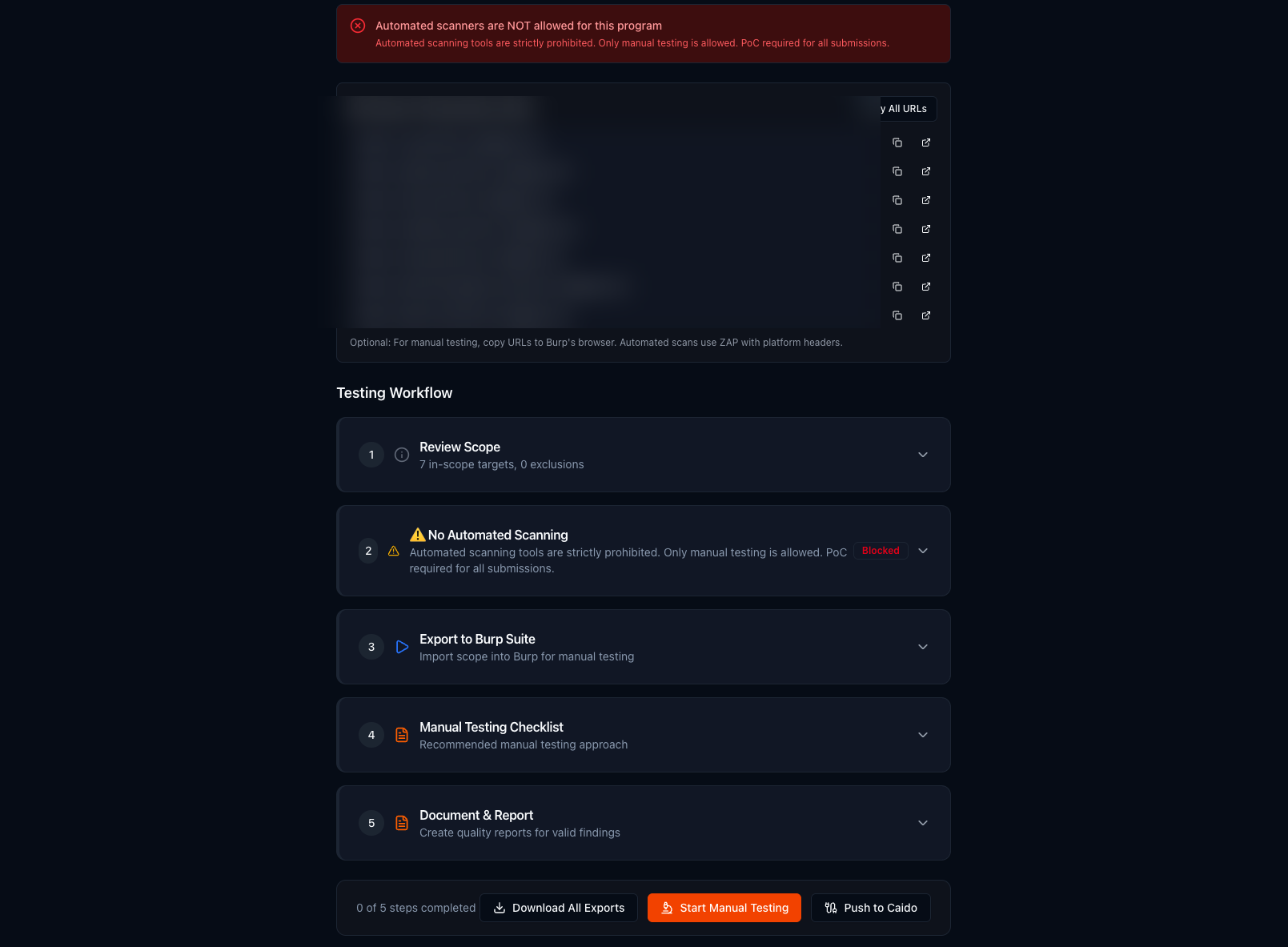
Import program scope and rules directly from bug bounty platforms. Guided testing workflow with Burp Suite and Caido integration, automated rule enforcement, and manual testing checklists.
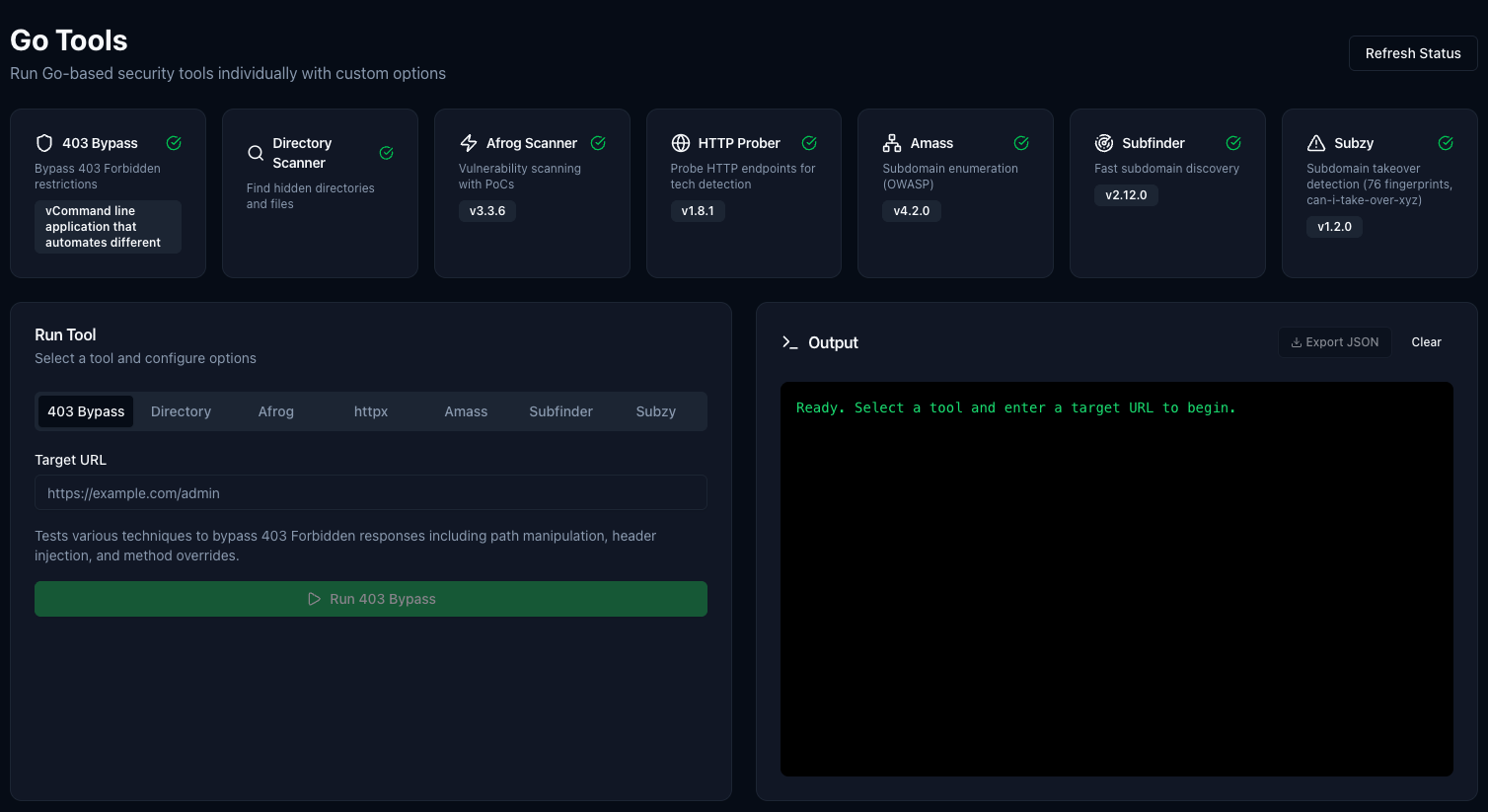
Integrated Go-based security tools — 403 bypass, directory scanning, vulnerability scanning with Afrog, HTTP probing, subdomain enumeration and takeover detection. One-click execution with JSON export.
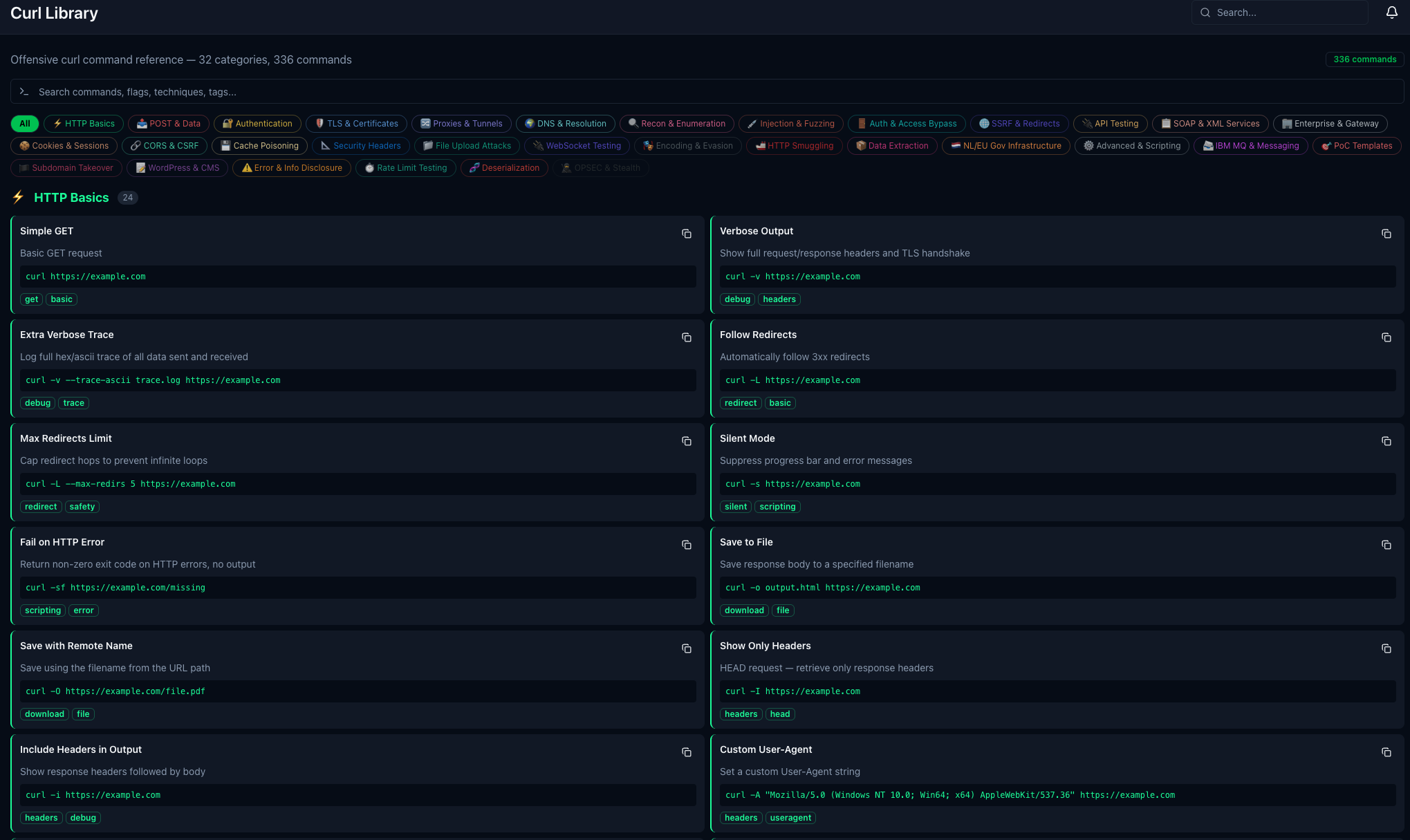
336 offensive curl commands across 32 categories — from HTTP basics to injection, SSRF, cache poisoning, smuggling, SOAP/XML services, and enterprise gateway testing. Searchable and copy-ready.
Areas of focus and expertise
Authentication bypass, broken access control, IDOR, CSRF, SSRF, XSS, and business logic flaws. Manual testing of session management, OAuth/OIDC flows, and multi-step workflows that scanners can't reach.
REST, SOAP/WS-*, and GraphQL testing with dedicated tooling. XXE via SOAP envelopes, WS-Addressing SSRF, GraphQL introspection abuse, mutation injection, broken object-level authorization, and API gateway bypass techniques.
Active hunter on enterprise and government programs. Focused on high-impact findings — authentication bypasses, data exposure, injection chains, and privilege escalation. CVD-compliant disclosure with structured PoC documentation.
API gateways (Layer7, Kong, WSO2), message brokers (IBM MQ, RabbitMQ), service meshes (Istio), container platforms (Kubernetes, OpenShift), and CI/CD pipelines. Testing what most testers skip.
A structured approach to every engagement
Asset discovery, technology fingerprinting, and attack surface mapping
Architecture review, authentication flow mapping, and threat modeling
Manual exploitation, automated scanning, and vulnerability validation
Clear findings documentation, risk scoring, and remediation guidance
How I handle your data and findings
Findings are never shared with third parties. All vulnerability details, evidence, and reports stay between you and me. WillardSec has no social media presence — by design.
All findings delivered in structured Markdown format — easy to integrate into your existing ticketing, documentation, or CI/CD workflows. No vendor lock-in, no proprietary formats.
All testing is performed remotely from my own office — no laptops or documentation are ever brought to client locations. Evidence stored locally, never in cloud services, and deleted after engagement closure.
Interested in a security assessment or collaboration?